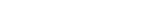Blogs

Future of Hosting: Predictions and Innovations in the Industry
July 11, 2023
Server Monitoring: The Only Guide You Will Ever Need
August 3, 2023The rapid adoption of cloud-based technologies by businesses are encouraging cyberattackers to target them. This is why we are seeing an exponential rise in cyberattacks targeting sensitive business data stored on the cloud. As more and more businesses migrate their workloads to the cloud, we will see the trend of growing number of cloud attacks continue.
How can you protect your business cloud data in such a situation? By keeping a close eye on the latest developments in the cloud industry. Permiso tried to provide you a sneak peek into the current state of cloud security through its cloud detection and response survey report 2023.
In this article, you will learn about seven key takeaways from cloud detection and response survey report 2023.
- 7 Key Takeaways From Cloud Detection and Response Survey Report 2023
- 1. Most Organziations Think That They Are Safe
- 2. Gaps in Threat Detection and Response
- 3. Faster Response
- 4. Slower Remediation
- 5. Cloud Security Posture Management and Native Cloud Security
- 6. Rising Complexity
- 7. Stolen Credentials Is Still The Biggest Threat
7 Key Takeaways From Cloud Detection and Response Survey Report 2023
Here are seven key takeaways from cloud detection and response survey report 2023.
1. Most Organziations Think That They Are Safe
According to the survey, 80% of organizations were confident that their current cloud tools and infrastructure is capable of protecting them from even a well executed attack on their cloud environment. That is exactly what attackers want businesses to think.
When businesses think that they are safe, they don’t do much to improve their cybersecurity defenses. In fact, they become relaxed, which gives cyberattackers an opportunity to strike.
Once they get their foot in the door, they can move laterally and compromise your entire cloud infrastructure. They use an attack vector to compromise a single account and use that account to gain access to other accounts. This leads to a never-ending vicious cycle.
2. Gaps in Threat Detection and Response
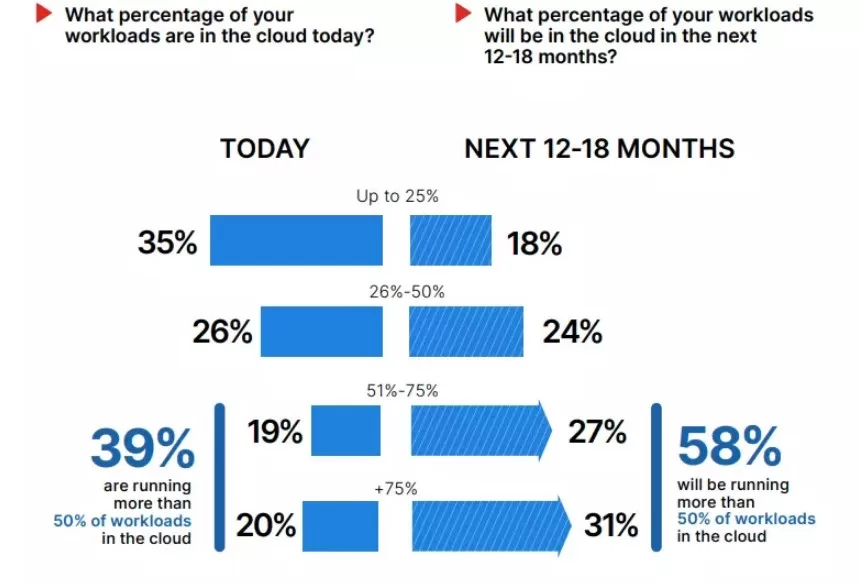
Despite this false sense of security, a vast majority of respondents were worried about their threat identification and response capabilities. In fact, 95% of organizations are concerned about the inefficiency of their current cloud security tools and cloud security teams in detecting threats and responding to these threats. This clearly shows that there is a lot of room for improvement when it comes to threat detection and response in the cloud.
3. Faster Response
The cloud detection and response survey also revealed that 70% of businesses were confident that they can respond to any cyberattack or data breach targeting their cloud infrastructure within 12 to 24 hours. Even though the response time might vary based on the nature of attacks, effectiveness of cybersecurity systems and many other factors, this is still an underestimation.
4. Slower Remediation
When Permiso collected data to verify this claim, they found that to be false. Incident response data collected and analyzed by Permiso showed that it took businesses more than two weeks, 16 days to be exact to fix the issue. This is a huge departure from the 12 to 24 hours response time businesses think they take to respond to threats. This is what gives them a false sense of cloud security, which can have devastating implications for them in the long run. This makes them complacent and consequently, a soft target for cybercriminals.
5. Cloud Security Posture Management and Native Cloud Security
The survey also found that 70% of businesses are already using a native cloud security solution and 48% are using a cloud security posture management solution to keep their cloud safe. Despite wider adoption of cloud native security and cloud security posture management, businesses still struggle to deal with cloud security threats. Did you know why? They don’t know how to make the most of these cloud security posture management and native cloud security tools.
These cybersecurity tools offer tons of useful features and security controls, which if used effectively can drastically minimize the risk of cloud attacks and data breaches. Not only that, these solutions can also help you boost your cybersecurity resilience and the maturity of your organization and enhance its cloud security capabilities.
6. Rising Complexity
Gone are the days when cloud environments used to contain a handful of entities and identities. Fast forward to today and they now contain thousands of them. According to the cloud detection and response survey, 80% of businesses have at least 1000 entities in their cloud environment.More than 60% have more than 1000 API secrets across the cloud infrastructure.
55% manage more than 5000 entities (cloud and on premises combined) while 31% have 2000 API secrets. Despite this, only 25% of businesses took advantage of federation capabilities to manage access in the cloud. That is why most businesses are struggling to maintain visibility over their cloud infrastructure. This makes it easy for threat actors to target them and steal sensitive business data stored in the cloud.
7. Stolen Credentials Is Still The Biggest Threat
Did you know what is the biggest threat to your cloud environment? It is stolen credentials. In fact, the cloud detection and response survey report found that stolen credentials are the primary attack vectors threat actors use to compromise your cloud data. That is why it is imperative for businesses to invest in an identity and access management solution.

It will give you more control over the cloud environment and let you decide who has access to which cloud data. Moreover, it also takes the pain out of identity management and makes the process hassle-free. Irrespective of how many identities and entities your cloud environment has, you can easily manage all of them without losing sight of any of them.
Even if you have an identity and access management system in place, that won’t guarantee you complete cloud protection. This is because most businesses don’t follow the best practices which is why they fail to take full advantage of identity and access management solutions.
This is evident from the methods businesses use to grant access to cloud environments. According to the cloud detection and response survey, 46% provided cloud console access to local identity and access management users while 38% used long keys to grant access to cloud environments, both of which are not secure methods for granting access.
Featured Post
IBM Unveils Solutions To Automate Security Operations
At RSA Conference 2025, IBM announced a significant expansion of its managed detection and response (MDR) services with the introduction of new agentic AI to automate […]
Why Are Strong Passwords Important in Cybersecurity?
Table of Contents The Role of Passwords in Cybersecurity Why Are Strong Passwords Important? Protection from Brute Force Attacks Preventing Account Hijacking Protecting Sensitive Information Safeguarding […]
7 Cybersecurity Trends for 2025 According to IBM
Table of Contents 7 Cybersecurity Trends for 2025 According to IBM 1. The Rise of Shadow AI 2. Identity Becomes the New Security Perimeter 3. Collaboration […]