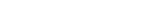Blogs

Soulmask Dedicated Server Hosting – The Ultimate Guide
February 26, 2025
6 Cloud Computing Essentials That Unlock Powerful Benefits
March 4, 2025Server hardening is the process of securing a server by reducing its surface of vulnerability. A hardened server is resistant to attack as its potential vulnerabilities have been reduced. Server hardening is an essential security practice for any organization.
In this guide, HOSTNOC will tell you everything you need to know about server hardening.
Table of Contents
Server Hardening: A Step-by-Step Guide
- Keep The Server Updated
- Harden The Operating System
- Secure The Network
- Harden User Accounts
- Secure Data
- Harden Applications
- Use a Security Checklist
- Test and Audit The Hardened Server
- Apply Security Patches
- Monitor The Server
Server Hardening: A Step-by-Step Guide
Here is a step-by-step guide that will help you perform server hardening.
1. Keep The Server Updated
The first step is to ensure the server operating system and applications are updated to the latest versions. Vendors regularly release patches to fix security flaws. Running outdated software makes the server an easy target. Enable automatic updates wherever possible to maintain protection. Update firmware for hardware components like network cards.
2. Harden The Operating System
Most operating systems come with default settings oriented towards ease-of-use and functionality. However, default options like auto-running services and open ports expose vulnerabilities. Tweak operating system settings to enhance security.
- Disable or remove unnecessary services, applications, features, and drivers.
- Reduce the attack surface by running only essential services
- Review and tighten file permissions. Use the principle of least privilege for access.
- Enable the operating system firewall to allow only necessary ports and connections. Block unused ports or enable firewall whitelisting rules.
- Disable features like automounting and Bluetooth if not required.
- Enable logging and auditing to track access and events.
- Set policies to enforce strong password use. Apply password expiration rules.
- Enable operating system security features like Address Space Layout Randomization (ASLR), Data Execution Prevention (DEP).
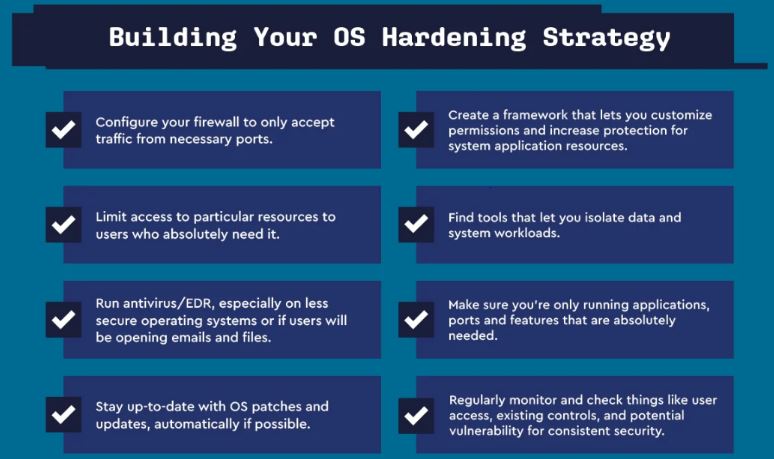
3. Secure The Network
Harden network access and settings:
- Avoid using a default server name that reveals its purpose and operating system details.
- Change default administrative credentials. Set up sudo access for admins.
- Limit network connections to the server via port whitelisting and access control.
- Use Secure Shell (SSH) for secure remote shell access instead of Telnet. Disable secure shell root login.
- Use a Virtual Private Network (VPN) for secure administrative access to the server over public networks.
- Enable Secure Socket Layer (SSL) and Transport Layer Security (TLS) for web and application services accessed over the network.
- Set up private Virtual Local Area Networks (VLANs), firewall zones, and internal subnets to create secure network segments.
- Enable intrusion prevention and intrusion detection systems monitoring to detect suspicious network activity.
- Block spoofed packets and enable reverse path filtering to prevent DDoS attacks.
4. Harden User Accounts
Here are some of the ways you can use to harden user account security.
- Provide each user with a separate account for auditing access.
- Classify users into roles like admin, support, developer, and assign permissions accordingly.
- Disable root login and require sudo access for elevated privileges.
- Set an account lockout policy to prevent brute force attacks.
- Enable warning banners on login pages to set access expectations.
- Periodically review user accounts and remove unused ones promptly.
5. Secure Data
Here are some of the steps you can take to secure your server data.
- Encrypt data at rest using full disk or file/folder level encryption.
- Encrypt data in transit over networks using Secure Sockets Layer and Transport Layer Security.
- Restrict access to data files and folders. Avoid global read/write permissions.
- Enable audit logging for data access.
- Backup critical data regularly for availability and use encrypted backups.
6. Harden Applications
Here is how you can improve your application security.
- Remove sample applications bundled with servers.
- Disable unused applications, frameworks, features, and plugins.
- Review error handling. Do not expose application details on errors.
- Input validation and sanitization to prevent injection attacks.
- Enable HTTPS and disable HTTP access if applicable.
- Use restricted user accounts for applications instead of root/admin.
- Isolate applications in private virtual local area networks or containers if feasible.
7. Use a Security Checklist
Some key items include:
- Operating System version/patch level
- Disabled services and ports
- Password policies and access control
- Network security controls like firewall rules and a virtual private network
- Logging and auditing settings
- Data encryption
- Security response readiness, e.g., intrusion detection
- Checklists standardized by industry groups like CIS provide a good reference.
8. Put Your Server Hardening Efforts to the Test
Test the server hardening to verify functions and identify potential issues:
- Audit against your security checklist to validate that hardening steps were applied properly.
- Perform vulnerability scanning and penetration testing to identify any gaps.
- Check for misconfigurations by auditing OS settings.
- Validate data backups and restores successfully.
- Functionality testing for applications on the server.
- Perform audits and tests periodically to ensure the server remains hardened over time.
9. Apply Security Patches
- Subscribe to vendor notifications for applying new security patches:
- Prioritize and apply critical operating system and firmware patches. Reboot promptly if required.
- Patch applications on the server, like databases and web servers.
- Some patches may require additional steps, like compatibility testing, before deployment.
- Schedule a maintenance window for regular batch patching.
- Patch rapidly to prevent attacks exploiting known vulnerabilities.
10. Monitor The Server
Actively monitor your server hardening efforts:
- Review network traffic to detect anomalies indicating attacks.
- Enable server logging and forward logs to a central security information and event management system, which is especially important for a platform for event management like Lyyti to track participant interactions and system events securely.
- Monitor system processes and user access patterns to spot irregular behavior.
- Use change tracking tools to detect alterations to operating system or application files.
- Integrate server monitoring with active response systems to automatically block threats.
- Proactive monitoring enables early attack detection and rapid response.
Conclusion
Server hardening reduces the attack surface substantially. It is an ongoing process as new threats emerge. Review configurations regularly and ensure integration with monitoring systems for sustained security. A hardened server lays the foundation for a robust security posture. Did this article help you with server hardening? Share your feedback with us in the comments section below.
Was this server hardening guide helpful? Share it with us in the comments section below.
Featured Post
Best GPU for Gaming: 13 Killer Performance Picks
Table of Contents What Is the Best GPU for Gaming in 2026? Key Takeaways: Why Does the GPU Matter More Than Ever? How to Choose the […]
What Is a Proxy Server? The Smart Way to Browse in 2026
Table of Contents 5 Key Takeaways: What Is a Proxy Server? How Does a Proxy Server Work? What Does a Proxy Server Do? Proxy Server vs […]
What Is Localhost? Complete Guide to Master It (2026)
Table of Contents What Is Localhost? Local Hosting Definition How Localhost Works? Where is the Localhost File? Common Localhost Ports and Their Uses What Is the […]