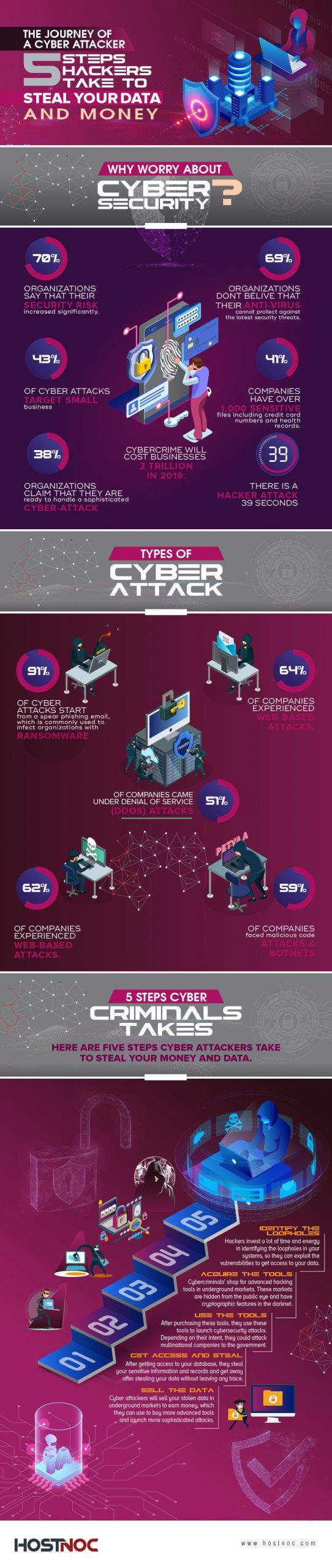
The Journey of a Cyber Attacker: 5 Steps Hackers Take To Steal Your Data and Money

7 Common Types of Phishing Attacks Cybercriminals are Launching During This Pandemic
April 13, 2020
4 Valuable Cybersecurity Lessons Businesses Can Learn From COVID-19 Pandemic
April 21, 2020With the news of cybersecurity attacks and data breaches getting media attention both in print and electronic media, businesses are worried about how they can keep their data safe. Even though cybersecurity experts are trying everything they can to fight off cyber-attacks, but hackers seem to be one step ahead of them in this race.
In order to protect your digital assets from prying eyes, you will have to get into the shoes of cyber attackers and think like a hacker. Know the process cybercriminals follow to launch cybersecurity attacks and it would put you in a better position to protect against such attacks. Which path do they follow to launch lethal cybersecurity attacks?
Here is an infographics that will highlight the path that cyber attackers follow to launch a cyber attack on your digital assets.