Sarmad Hasan
Featured Post
See moreSelecting the right server hardware is crucial for any business looking to set up a server environment. The components you choose will impact performance, scalability and […]
Server operating systems (OS) form the critical backbone of modern IT infrastructure, providing the platform to manage hardware resources, host applications and handle multiple client requests […]
The digital landscape is evolving. The Future of Web Hosting industry is experiencing significant changes that promise to reshape the future of online presence. From advancements […]
Updates
See moreAffiliate marketing blog is a dynamic and ever-evolving field, with trends, strategies, and technologies constantly changing. To stay ahead of the curve and ensure success, it […]
As we gear up to Celebrate Independence Day 4th of July, HOSTNOC is excited to announce a special Celebrate Independence Day 4th of July that will light […]
The RSA Conference 2024, themed “The Art of Possible” took place from May 6 2024 to May 9 2024, promising insights into emerging trends and skills. […]
Dedicated Server
See moreAs businesses continue to navigate the digital transformation journey, server technologies are evolving to meet growing demands for performance, efficiency and security. In 2025, the server […]
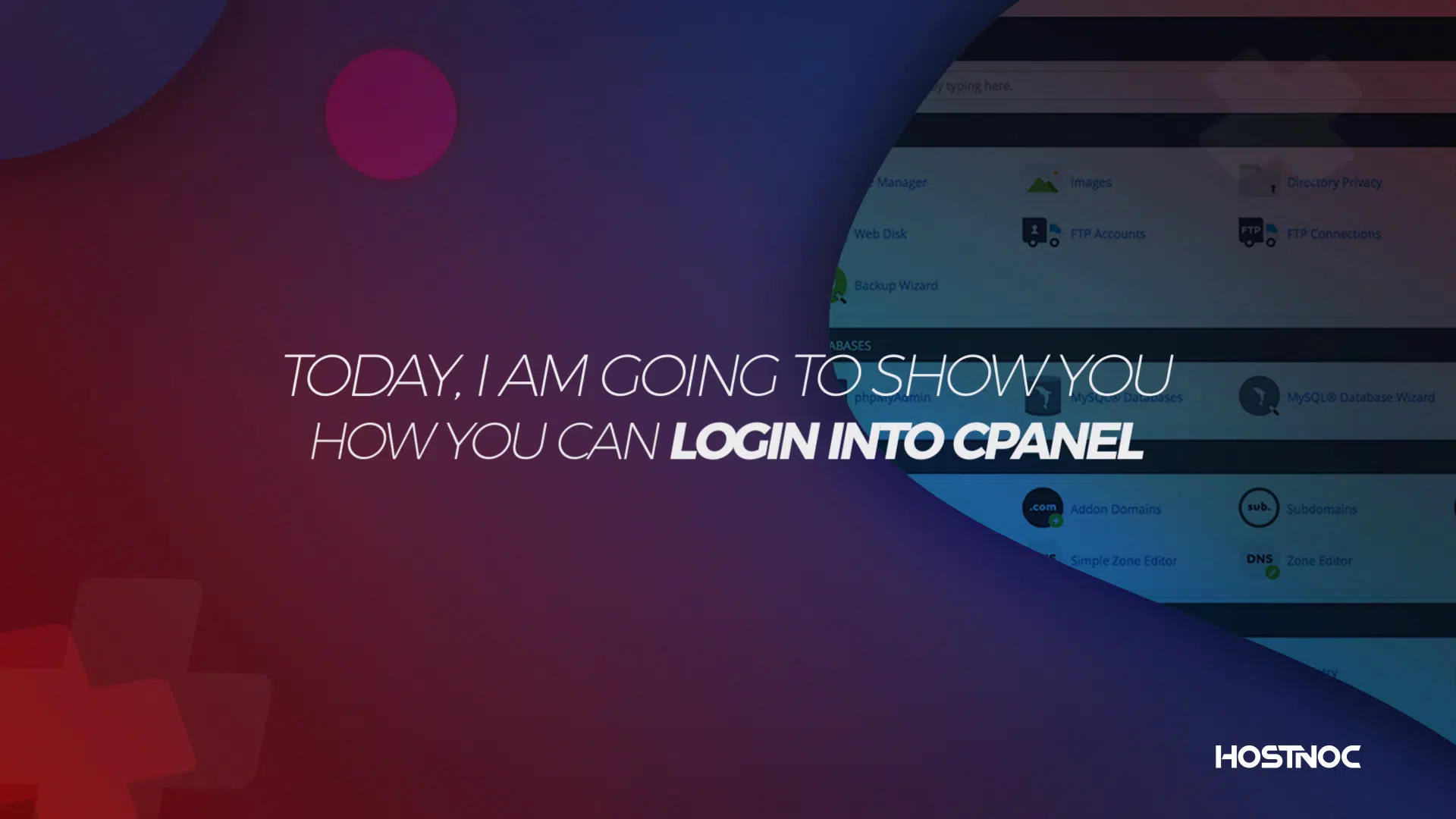
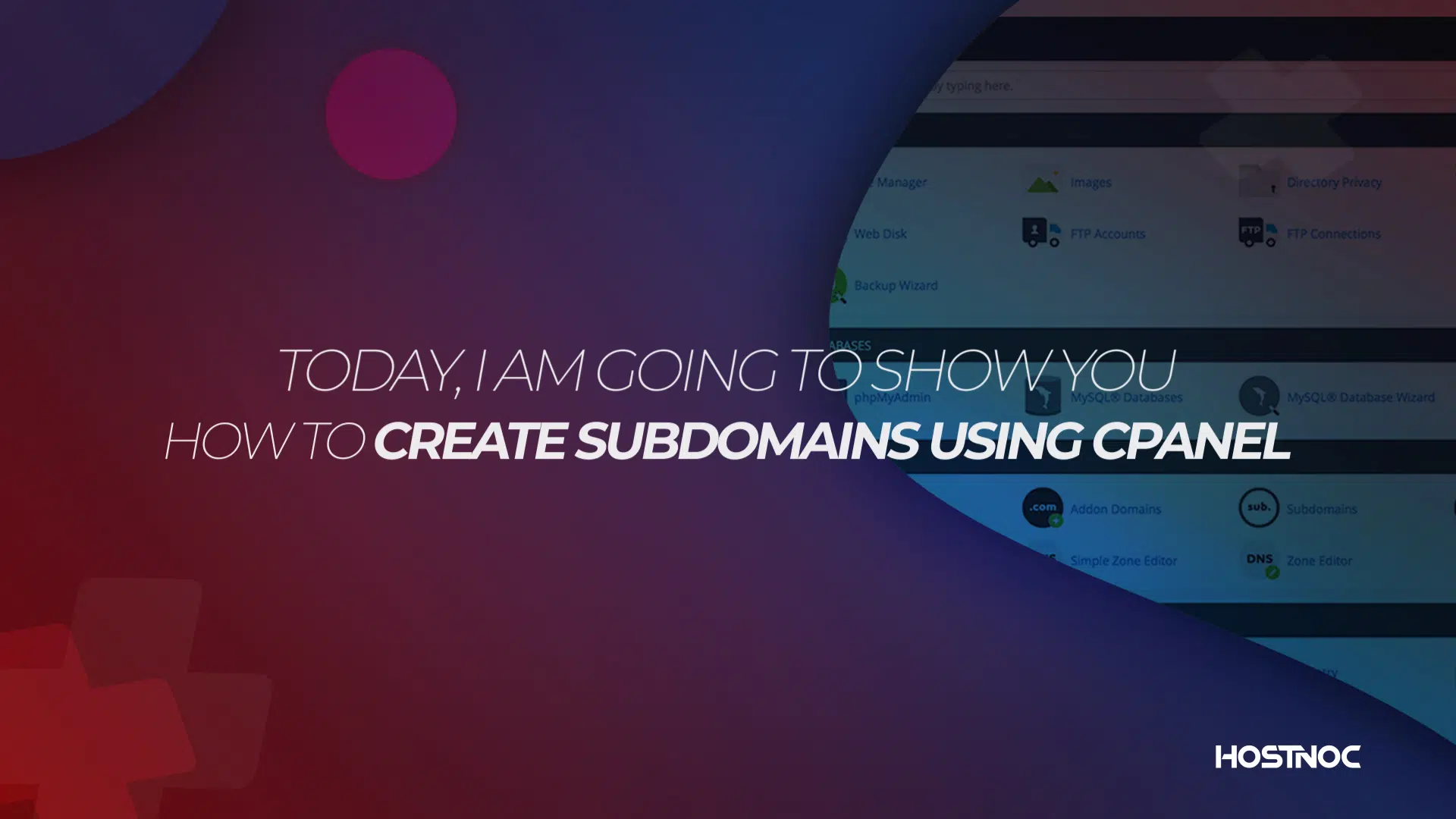
Whether you are setting up a server for a personal project or managing servers for a large organization, understanding how to properly configure your server can […]
In the vast landscape of the internet, users often encounter various error codes that disrupt their seamless online experiences. One such error code that might seem […]
Wordpress
See moreYou are in a hurry and want to get some information from the internet. You search the internet and click on the link that looks more […]
After launching WordPress 5.9 a few months back, which brought much-needed improvements to the editing experience, WordPress is taking things a step further by integrating full […]
Security Monitoring
See moreIn today’s rapidly evolving digital landscape, Cloud Security computing has emerged as a transformative force, offering organizations unmatched scalability, flexibility, and cost-efficiency. However, amidst the boundless […]
You might be familiar with Software as a Service (SaaS), Platform as a Service (PaaS) and Infrastructure as a Service (IaaS) but have you ever heard […]
Did you know that 85% of all emails are spam? According to email spam statistics, 122.33 billion email messages are sent every day. In fact, the […]
Cloud Management
See moreCloud Cost Optimization offers tremendous benefits in scalability, flexibility and cost-efficiency. However, it’s easy to make mistakes that can lead to unexpected costs swelling your cloud […]
According to Accenture data, Only 44% of businesses have adopted the cloud globally. This means that there are still 56% of businesses who have not adopted […]
In today’s rapidly evolving digital landscape, Cloud Security computing has emerged as a transformative force, offering organizations unmatched scalability, flexibility, and cost-efficiency. However, amidst the boundless […]